Community Feature - @captainGeech42
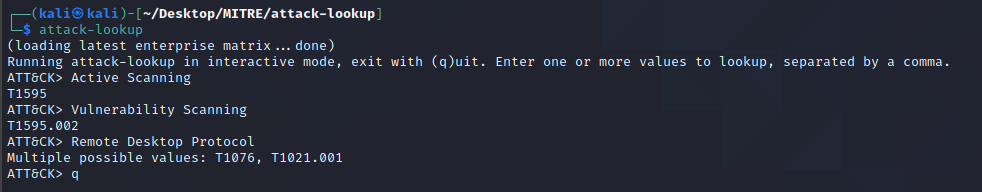
A Curated Intelligence member - Zander Work - has developed a new tool for looking up the "T" codes for techniques present on the MITRE ATT&CK framework. This tool is used by CTI analysts, DFIR investigators, and SOC analysts to quickly identify and map tactics, techniques, and procedures (TTPs).
https://github.com/curated-intel/attack-lookup
Cyber Threat Intelligence is knowledge about adversaries and their motivations, intentions, and methods that is collected, analysed, and disseminated in ways that help security and business staff at all levels protect the critical assets of the enterprise. The ATT&CK Lookup tool helps CTI analysts take another step towards this goal.
Demonstration of the tool in action:
Curated Intel Community Features are sourced using our Member Content channel on Discord. If you have recently produced a noteworthy piece of writing, a project, a podcast, an infographic or other CTI content let us know!